Website Vulnerability scan

Why is website vulnerability scanning critical?
Every day, attackers exploit weak points in websites to steal data, inject malicious code, or take systems offline. These vulnerabilities are often the result of outdated software, misconfigurations, or code level flaws that go undetected until it’s too late.
What vulnerability scan does
Key Benefits

Minimize risk of cyberattacks
By identifying vulnerabilities early, vulnerability scanning plays a critical role in significantly reducing your exposure to a wide range of exploits, such as SQL injection, cross-site scripting (XSS), insecure configurations, and many others. Through proactive detection, organizations can address weaknesses before malicious actors have the opportunity to exploit them. Regular scanning not only strengthens your overall security posture but also ensures compliance with industry standards and best practices. By catching vulnerabilities at an early stage, you minimize potential damage, protect sensitive data, and maintain the trust of your customers and stakeholders. In today’s evolving threat landscape, early detection is a key pillar of effective cybersecurity defense.

Stay ahead of the threat landscape
Our advanced scanning engine is continuously updated with the latest CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) intelligence, ensuring comprehensive protection against emerging and evolving threats. By leveraging real-time vulnerability data, we proactively identify and mitigate potential risks before they can be exploited. This dynamic approach enables us to offer cutting-edge security coverage, helping you stay one step ahead in an increasingly complex threat landscape. With our technology, you can trust that your systems are shielded against the most recent, relevant, and critical security challenges.
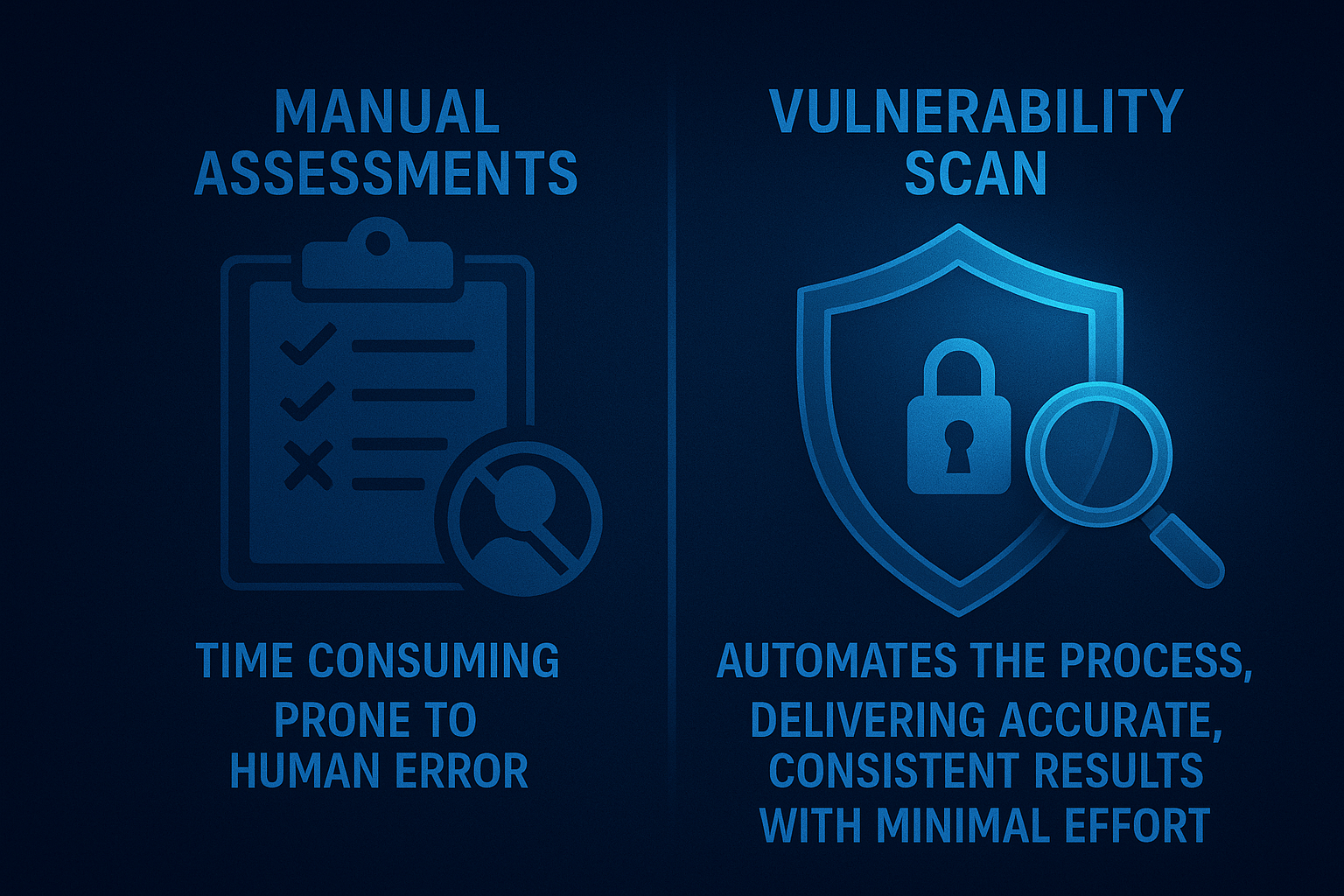
Save time and resources
Manual vulnerability assessments, while valuable, are often time-consuming, labor-intensive, and prone to human error. Analysts may overlook critical issues, misinterpret results, or experience fatigue, all of which can compromise the overall security evaluation. Vulnerability scanning automates this process, ensuring accurate, reliable, and consistent detection of weaknesses across your systems. By eliminating manual inefficiencies, automated scans not only save significant time and resources but also enhance the precision and coverage of your security efforts. With minimal effort, organizations can maintain a high level of vigilance and respond quickly to emerging threats.

Actionable reports for fast remediation
Each vulnerability report provides comprehensive and easy-to-understand descriptions of the identified security issues, eliminating the need for guesswork or interpretation. Every vulnerability is clearly outlined with details about its nature, severity rating, and potential impact on your systems and data. Additionally, the report includes actionable, step-by-step recommendations for how to effectively resolve each issue. This empowers your security and IT teams to prioritize fixes based on risk and implement solutions efficiently. With clear guidance and expert-driven insights, you can strengthen your security posture faster and more confidently.

Continuous protection with scheduled scans
Security is not a one-time task; it requires continuous attention and proactive management. With ongoing vulnerability scans, your organization benefits from a dynamic defense system that evolves alongside your technology stack and responds to newly emerging threats. As updates, new features, and third-party integrations are introduced, fresh vulnerabilities can surface — and our continuous scanning ensures they are identified and addressed promptly. Regular assessments help maintain a strong security posture, preventing outdated protections from creating weak points. By integrating ongoing vulnerability scanning into your security strategy, you build a resilient, adaptive defense that keeps your digital assets safeguarded at all times.
Key Features
Automated scanning
Regular crawling and analysis of your website to detect vulnerabilities
Detailed reporting
Easy to understand reports with prioritized risk levels and remediation suggestions
CVE/CWE integration
Detection based on industry standard databases and classification systems
Continuous monitoring
Scans are scheduled to run at defined intervals for ongoing protection
Real time risk visibility
Understand your current security posture and act quickly to address gaps
Who should use Vulnerability?
- E-commerce websites
- SaaS platforms
- MSPs and security consultants
- SaaS platforms
- Healthcare and compliance-driven industries

Don’t wait for a breach to expose your weaknesses
“Eye World has played a vital part in our efforts to create the ultimate customer experience”
Siv Bayegan, Business Manager Future Services, Telenor