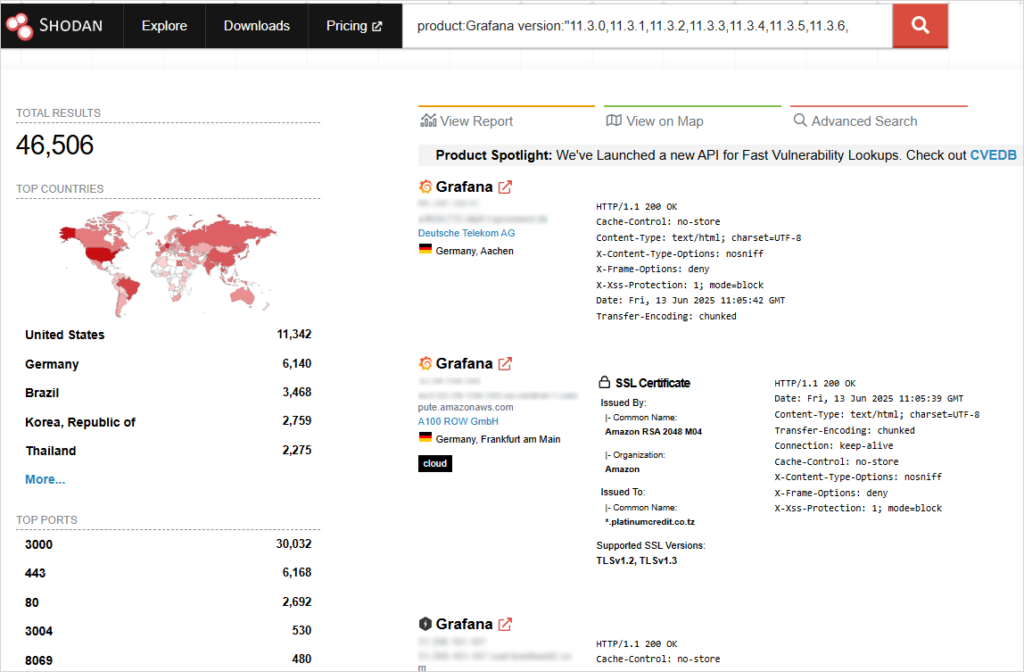
More than 46,000 online-facing Grafana instances are still unpatched and vulnerable to CVE-2025-4123—a serious client-side flaw. This open redirect vulnerability allows attackers to load malicious plugins, hijack user sessions, and potentially take control of user accounts. Despite a fix released on May 21, many organizations have yet to upgrade, according to research by OX Security.
The exploit, named The Grafana Ghost, can be triggered without login credentials. It combines client-side path traversal with redirect manipulation. When users click a crafted link during an active session, attackers can inject JavaScript, change email settings, and bypass password recovery processes.
Default protections like Grafana’s Content Security Policy (CSP) do not stop this exploit. The flaw misuses internal routing logic to bypass browser safeguards. Over 128,000 Grafana instances were scanned—36% are still running vulnerable versions.
How the Exploit Works and Why It’s Dangerous
This bug relies on crafted URLs that redirect users to malicious sites. From there, the attacker’s server can serve unauthorized plugins, which run in the user’s browser. Even when anonymous access is enabled, the exploit remains effective—making it especially dangerous in large-scale deployments.
If the Grafana Image Renderer plugin is installed, attackers can use Server-Side Request Forgery (SSRF) to access internal network data. The impact includes hijacked accounts, modified credentials, and full session control—all from a single user click.
The attack requires user interaction, but the scale of exposed systems and lack of authentication make this vulnerability a major threat to infrastructure monitoring environments.
Eye World Urges Immediate Patch to Stop the Grafana Ghost
To mitigate this issue, Eye World strongly advises Grafana administrators to upgrade immediately. The following patched versions address CVE-2025-4123:
- 10.4.18+security-01
- 11.2.9+security-01
- 11.3.6+security-01
- 11.4.4+security-01
- 11.5.4+security-01
- 11.6.1+security-01
- 12.0.0+security-01
Disabling unused plugins and reviewing anonymous access settings are also recommended. Organizations should regularly scan for known vulnerabilities and apply security updates promptly. Staying ahead of threats like The Grafana Ghost is essential to protect monitoring environments from silent breaches.

